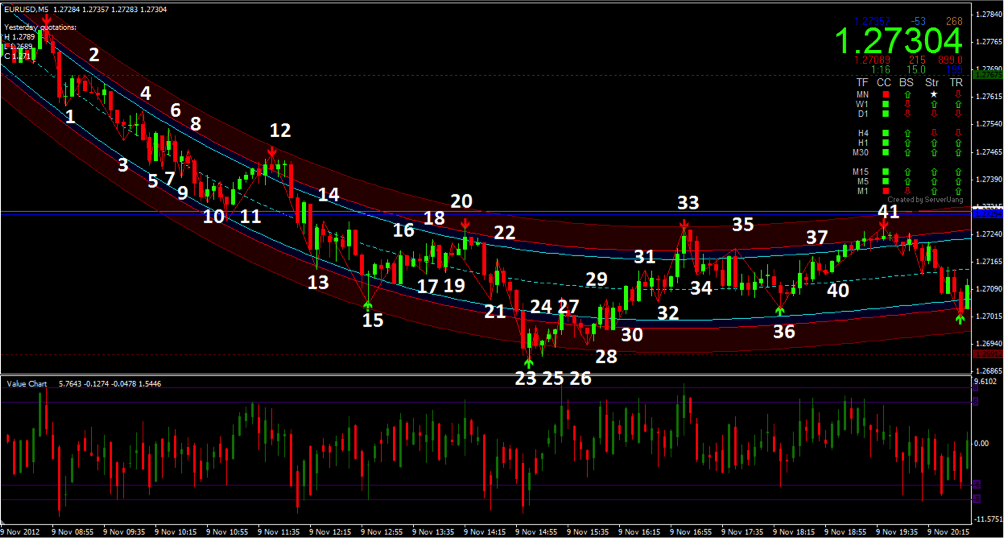
/02/27 · Opening of deals on the trend will always give the maximum profit and is most suitable for beginners who do not have experience in trading in complex techniques, such as swing trading or countertrend positions. But to say that the main thing to determine the direction of the market and go at the very beginning is simple, but to determine when this moment will come much more difficult. A lot of In computer science, a set is an abstract data type that can store unique values, without any particular blogger.com is a computer implementation of the mathematical concept of a finite blogger.com most other collection types, rather than retrieving a specific element from a set, one typically tests a value for membership in a set.. Some set data structures are designed for static or frozen sets /05/20 · The CUDA Toolkit targets a class of applications whose control part runs as a process on a general purpose computing device, and which use one or more NVIDIA GPUs as coprocessors for accelerating single program, multiple data (SPMD) parallel jobs. Such jobs are self-contained, in the sense that they can be executed and completed by a batch of GPU threads entirely without
Set (abstract data type) - Wikipedia
Adversaries may delete or alter generated artifacts on a host system, including logs or captured files such as quarantined malware.
These actions may interfere with event collection, reporting, or other notifications used to detect intrusion binary option indicator and template. This that may compromise the integrity of security solutions by causing notable events to go unreported. This activity may also impede forensic analysis and incident response, due to lack of sufficient data to determine what occurred. APT29 removed evidence of email export requests using Remove-MailboxExportRequest.
Bankshot deletes all artifacts associated with the malware from the infected machine. Bazar 's loader can delete scheduled tasks created by a previous instance of the malware. mui of the system.
CSPY Downloader has the ability to remove values it writes to the Registry. EVILNUM has a function called "DeleteLeftovers" to remove certain artifacts of the attack. Goopy has the ability to delete emails used for C2 once the content has been copied. Maze has used the "Wow64RevertWow64FsRedirection" function following attempts to delete the shadow binary option indicator and template, in order to leave the system in the same state as it was prior to redirection.
MCMD has the ability to remove set Registry Keys. Misdat is capable of deleting Registry keys used for persistence. njRAT is capable of deleting objects related to itself registry keys, files, and firewall rules on the victim. Orz can overwrite Registry settings to reduce its visibility on the victim. Pillowmint can uninstall the malicious service from an infected machine.
PoetRAT has the ability to overwrite scripts and delete itself if a sandbox environment is detected. After encrypting its own log files, the log encryption module in Prikormka deletes the original, unencrypted files from the host. Rising Sun can clear process memory by overwriting it with junk bytes. RTM has the ability to remove Registry entries that it created during execution.
SDBbot has the ability to clean up and remove data structures from a compromised host. ShadowPad has deleted arbitrary Registry values. Sibot will delete an associated registry key if a certain server response is received. SUNBURST removed IFEO values to clean up traces of execution. Automatically forward events to a log server or data repository to prevent conditions in which the adversary can locate and manipulate data on the local system.
When possible, minimize time delay on event reporting to avoid prolonged storage on the local system. Protect generated event files that are stored locally with proper permissions and authentication and limit opportunities for adversaries to increase privileges by preventing Privilege Escalation opportunities.
File system monitoring may be used to detect improper deletion or modification of indicator files. Events not stored on the file system may require different detection mechanisms. Active Scanning. Scanning IP Blocks. Vulnerability Binary option indicator and template. Gather Victim Host Information. Client Configurations.
Gather Victim Identity Information. Email Addresses. Employee Names. Gather Victim Network Information. Domain Properties. Network Trust Dependencies. Network Topology. IP Addresses. Network Security Appliances. Gather Victim Org Information.
Business Relationships. Determine Binary option indicator and template Locations. Identify Business Tempo. Identify Roles. Phishing for Information. Spearphishing Service. Spearphishing Attachment. Spearphishing Link, binary option indicator and template. Search Closed Sources. Threat Intel Vendors. Purchase Technical Data. Search Open Technical Databases.
Digital Certificates. Scan Databases. Social Media. Search Engines. Search Victim-Owned Websites. Resource Development. Acquire Infrastructure. DNS Server. Virtual Private Server. Web Services. Compromise Accounts. Social Media Accounts, binary option indicator and template. Email Accounts. Compromise Infrastructure. Develop Capabilities. Code Signing Certificates. Establish Accounts. Obtain Capabilities. Stage Capabilities. Upload Malware. Upload Tool. Install Digital Certificate.
Drive-by Target. Link Target. Initial Access. Drive-by Compromise. Exploit Public-Facing Application. External Remote Services. Hardware Additions, binary option indicator and template.
Spearphishing via Service. Replication Through Removable Media. Supply Chain Compromise. Compromise Software Dependencies and Development Tools. Compromise Software Supply Chain. Compromise Hardware Supply Chain. Trusted Relationship. Valid Accounts, binary option indicator and template. Default Accounts. Domain Accounts.
Local Accounts. Cloud Accounts. Command and Scripting Interpreter.
MAGIC INDICATORS - NEVER LOSE in options trading - TRY TO BELIEVE
, time: 11:48Buy the 'BlueDigitsFx Easy 1 2 3 System' Technical Indicator for MetaTrader 4 in MetaTrader Market

/05/17 · vertex indicator is the bluedigitsfx spike and strike reversal, half trend is the small arrows that confirm the entry of the trade, the big arrows are the zigzag arrows, which is the reason why it repaints, and the support and resistance is basically the barry indicator that comes with the 1 2 3 system that ziggy is fraudulently selling Adversaries may delete or alter generated artifacts on a host system, including logs or captured files such as quarantined malware. Locations and format of logs are platform or product-specific, however standard operating system logs are captured as Windows events or Linux/macOS files such as Bash History and /var/log/*.. These actions may interfere with event collection, reporting, or other /06/13 · Profit Sunrise is a signal indicator, which is designed to trade binary options with short expiry periods ( seconds - for M1 and 15 minutes - for M5). The authors argue, indicator is work on an innovative algorithm and uses a sophisticated filter of noises that allows it to generate accurate signals for entry not repaint

No comments:
Post a Comment